Sumo Logic ahead of the pack
Read article
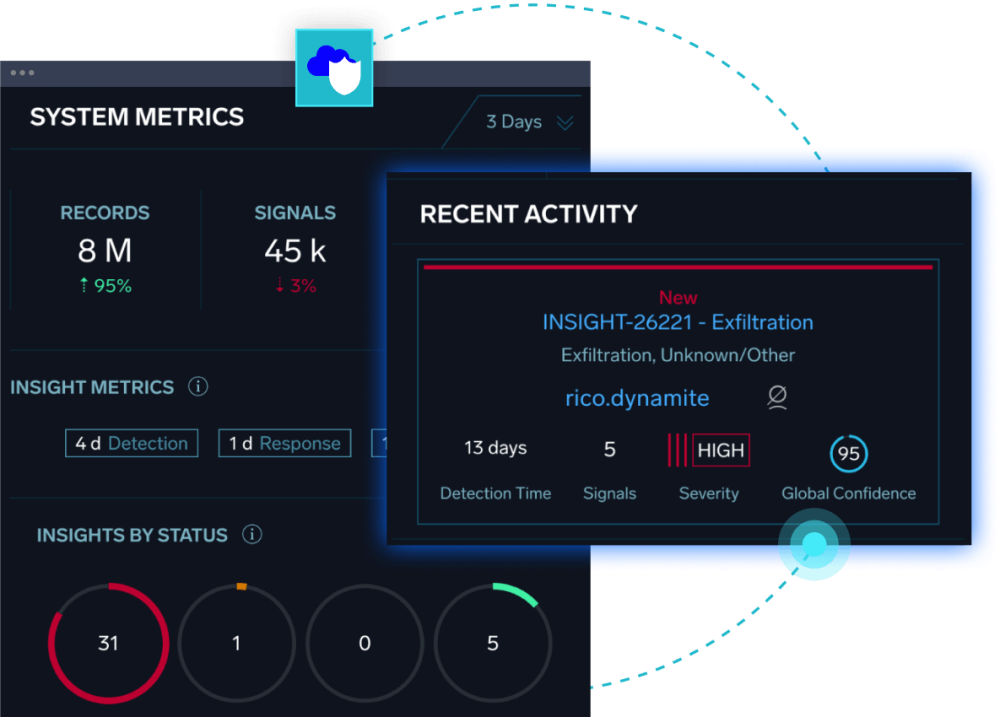
Revolutionize your security.
The better SIEM solution is here.
Sumo Logic Cloud SIEM provides security analysts and SOC managers with enhanced visibility across the enterprise to thoroughly understand the scope and context of an attack. Streamlined workflows automatically triage alerts to detect known and unknown threats faster.